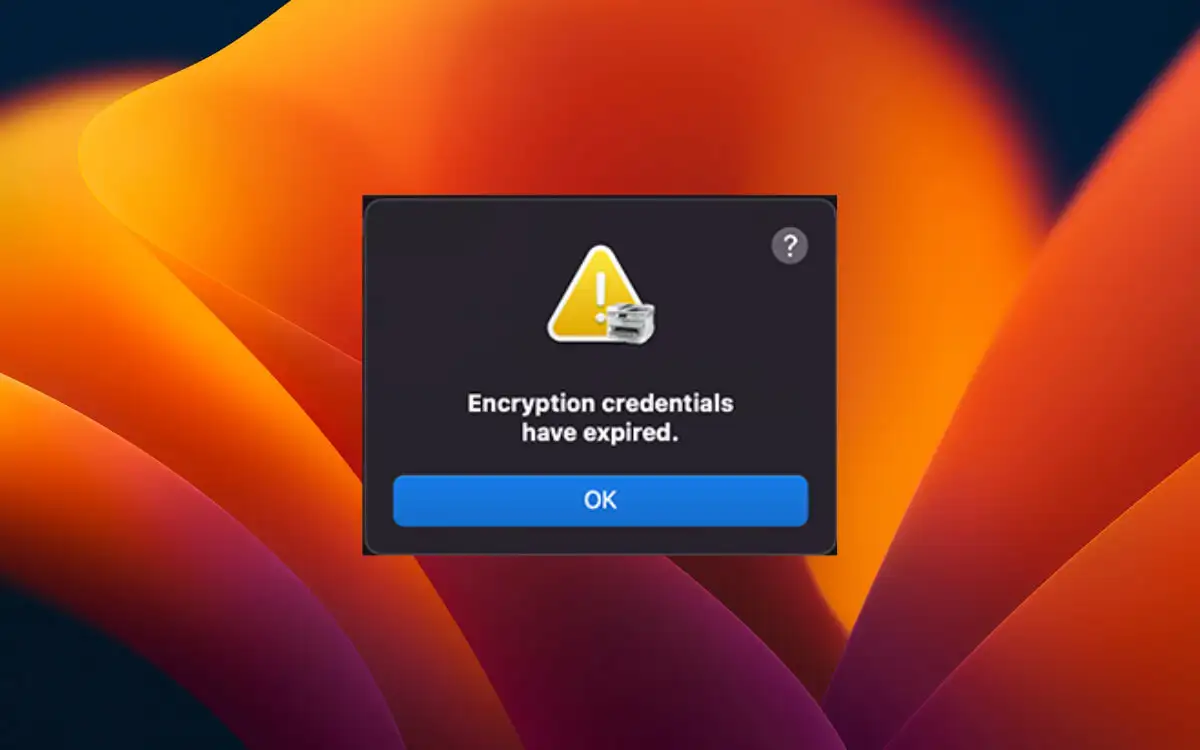
Encryption credentials have expired
Introduction
Encryption credentials have expired, The significance of encryption credentials, the reasons in the back of their expiration, and strategies for managing and lowering problems in the constantly converting area of virtual security are all included in the article.
Understanding Encryption Credentials
Credentials for encryption are the foundation of safe online communication. They cover a variety of authentication components, such as tokens, digital certificates, and cryptographic keys. These credentials are essential for protecting data both during transmission and storage since they guarantee that sensitive data can only be accessed and decoded by authorized parties.
Common Causes of Expiry
Time-Based Validity:
Frequently, encryption credentials have a set lifetime. A security feature that lowers the possibility of credentials being hacked over time is time-based validity.
Security Policy Compliance:
Security rules that require encryption credential renewal regularly are implemented by organizations. This procedure guarantees the stability of cryptographic keys and certificates while adhering to standard practices.
Changes in Encryption Systems:
The need for current credentials to expire may arise from updates or modifications made to encryption systems. This guarantees that the system will work with updated security methods and technology.
Implications of Expired Encryption Credentials
Data Access Issues:
Users could have trouble gaining access to systems secured by expired credentials or encrypted data, which might cause workflow disruptions and perhaps result in data loss.
Security Vulnerabilities:
Credentials that have expired create security risks since they might be more vulnerable to hacking or illegal access. The integrity and security of sensitive data are in danger because of this.
Addressing the Issue: Renewal and Update Procedures
Stay Informed:
Check emails, alerts, and system notifications often for information that might give you a heads-up on when your credentials are about to expire.
Navigate to Credential Management Interface:
Enter the system or interface for managing credentials, which is usually supplied by the company or service provider.
Review and Renew:
Examine the current credentials’ status and adhere to the system’s recommended renewal or updating processes. This might entail getting new tokens, upgrading certificates, or creating new cryptographic keys.
Follow Organizational Policies:
Respect the policies of the organization on the renewal of credentials. Organizations frequently offer policies and deadlines for preserving the confidentiality of encryption credentials.
Troubleshooting Expiry Issues
Check System Logs:
Look through the system logs for any alarms or error messages about expired credentials. This may shed light on the problem’s underlying causes.
Contact Support:
If attempting troubleshooting on your own proves difficult, ask for help from the applicable service or system’s support staff.
Collaborate with IT:
To resolve the issue, collaborate closely with the IT department of your company. They can offer direction, updates, or put fixes in place to fix the expired credentials..
Security Best Practices for Credential Management
Periodic Reviews: Make that encryption credentials are current and adhere to security guidelines by conducting periodic reviews.
Automated Renewal Procedures: Whenever practical, use automated procedures to renew credentials. Expiration dates are less likely to be overlooked when processes are automated.
Knowledge and Consciousness:
Inform users of the value of managing their encryption credentials. Encourage adherence to corporate standards, the establishment of secure passwords, and best practices for security.
Future Developments and Improvements
Developments in Credential Management: Keep up with developments in technology and systems for credential management that might simplify the renewal procedure and improve security in general.
User-Friendly Interfaces: Promote the use of user-friendly interfaces to make it easier to navigate the credential renewal procedure and lower the risk of errors.
FAQs (Frequently Asked Questions)
What does it mean when I receive the message “Encryption Credentials Have Expired”?
This message indicates that the cryptographic keys, certificates, or other authentication elements used for encrypting and securing data have reached the end of their designated lifespan and need to be renewed.
Why do encryption credentials expire?
Encryption credentials often have a predetermined lifespan as a security measure. This time-based validity helps reduce the risk of compromised credentials over extended periods, ensuring that cryptographic keys and certificates remain robust.
How do I renew expired encryption credentials?
To renew expired encryption credentials, navigate to the designated credential management interface provided by your organization or service provider. Review the status of existing credentials and follow the renewal or update procedures outlined in the system, which may involve generating new cryptographic keys, updating certificates, or obtaining fresh tokens.
What are the common causes of encryption credential expiry?
Encryption credentials may expire due to time-based validity, adherence to security policies, or changes in encryption systems. Regular updates and changes to security protocols may necessitate the expiration of existing credentials to ensure compatibility with upgraded technologies.
What are the implications of having expired encryption credentials?
Expired encryption credentials can lead to data access issues, disrupting workflows and potentially causing data loss. Additionally, they introduce security vulnerabilities, making systems more susceptible to unauthorized access or cyberattacks.
Conclusion
The expiration of encryption credentials is a tremendous problem in the digital safety panorama. These credentials are important for preserving the integrity and confidentiality of touchy records. The reasons behind their expiration are planned, which include time-primarily based validity, adherence to safety guidelines, and diversifications to evolving encryption structures. To remedy those demanding situations, proactive renewal and update techniques are important. Users should stay informed, navigate to special credential management interfaces, and comply with organizational policies for renewal. Troubleshooting, checking device logs, and searching for a guide from the government are critical steps. Adhering to protection first-class practices, which include ordinary opinions, automatic renewal approaches, and user training, is crucial. As virtual safety evolves, advancements in credential management technology and consumer-pleasant interfaces are anticipated. By understanding the motives behind expiration, adopting proactive renewal strategies, and embracing protection great practices, customers and organizations can navigate those demanding situations with resilience.
Read More=The Ultimate Guide to Mastering Encrypted Cipher Quests Fortnite